Oh, the wonderful world of Alibaba!
Just like the old tale, a trip to Alibaba’s website can either unearth many treasures or lead you down a path to destruction.
Either way, buying from Alibaba can be quite the adventure.
Your first visit to Alibaba can be a little intimidating. You’ve probably heard stories of people being scammed on the website and are probably wondering if it could happen to you.
If you are looking for Dropshipping Suppliers, better jump to our other article Best Dropshipping Companies to consider Alibaba alternatives.
Quick verdict:
Here’s the truth:
Shopping from Alibaba is relatively safe if you know where to shop from. There are good and honest suppliers on Alibaba, but there are also a few undesirables lurking on the platform. That's a usual sight in any marketplace.
- Quick verdict:
- Alibaba Pros and Cons
- What is Alibaba and How Does it Work?
- What’s the difference between Alibaba and AliExpress?
- How Does Alibaba Work?
- Is Alibaba Safe?
- How to Make Alibaba Safer
- Trade Assurance Can Save You Money
- Choose Gold Suppliers
- Make Sure That There Has Been a Supplier Assessment
- Validate What They’re Saying About Themselves
- What Are Other People Saying About Your Supplier
- You Cannot, I Repeat, Cannot Buy Branded Items Wholesale From Alibaba
- Check Out The Company’s History
- There’s a Difference Between Manufacturers and Traders
- Make Sure You’re Ready To Receive The Shipment
- Alibaba Review: Conclusion
What if I told you that there is a way for you to have an enjoyable, secure, and profitable experience through Alibaba by spending an extra two minutes? I can guarantee your safety.
Well, read on to find out how you can have a great buying experience from Alibaba.
Alibaba Pros and Cons
As a tool for business growth and development, Alibaba has a selection of pros and cons to consider. First and foremost, it’s a low cost way to get items for your product portfolio and sell them to your customers. However, it’s also worth noting that there are a lot of complications to handle in the process with things like middlemen and wire transfer requirements.
Let’s have a look at some of the pros and cons associated with this business model.
Pros 👍
- The wholesale prices from Alibaba are very low, which increases your potential profit margins.
- There are millions of possible products to choose from, with Alibaba reviews to help you make your decision.
- You can assess potential suppliers based on their status with Alibaba trade assurance. This reduces your risk of buying from the wrong company.
- You can have more control over your product packaging and shipping practices, which means that you can focus on delivering a good customer experience.
- You can deliver money through Alipay and western union bank transfer depending on your needs, which makes it easier to keep track of purchase.
- You can monitor the quality of your products before they reach your customers.
- Some manufacturers will allow you to access extra features like tracking your orders.
Cons 👎
- As a wholesale provider, Alibaba does come with a minimum order requirement. For some suppliers, the numbers can be in the hundreds. If you’re not sure of the quality of the items straight away, this is a risk.
- You could face legal action if you sell products that aren’t officially licensed but look like they belong to another company.
- The photos on the website don’t always match exactly what the customer might get. Product quality can often differ with Alibaba suppliers.
- Some niches will have their own obstacles to consider. For instance, clothing sizes in Asia are often smaller than they are in the US.
- When your items arrive, they won’t always work as they should. It can be difficult to organize refunds and returns when this happens.
- It’s complicated to get a refund sorted when your customer decides that they don’t want the item that you’ve sent them.
- You can’t start selling the moment you place your order. Plus, if you sell out of a certain item, it takes a while for you to regain that stock. This could lead to problems with customers who don’t want to wait around.
What is Alibaba and How Does it Work?

Alibaba is a unique solution for resellers and dropshipping businesses around the world. Founded by Jack Ma and another 17 co-founders in 1999, the Alibaba website introduced a new business-to-business solution for eCommerce. The idea behind this creation was to develop an environment where Chinese manufacturers could interact with international buyers.
The Alibaba.com experience is a phenomenal success. Acting in a way similar to Amazon, it allows people to stock up on crucial items for their stores. Once you choose your Alibaba items, you can work through a dropshipping partnership to have them sent directly to customers. This reduces the issues associated with storing your products and fulfilling orders.
Currently, Alibaba group holdings is one of the biggest companies in the world, and China that provides b2b, b2c, and c2c sales. It’s sparked a variety of other companies to follow suit.
With Alibaba, you don’t have to rely on eBay when you’re searching for suppliers for the first time. This website is one of the most popular ecommerce sites in the world. With it, small business owners can find a reliable supplier for all of their selling needs.
Depending on your needs, you can either buy a single item from Alibaba, or agree to sell with a manufacturer using a dropshipping methods. People who use Alibaba for dropshipping often benefit from high-volume discounts. You can also create some of your own designs too.
What’s the difference between Alibaba and AliExpress?
If you’ve been looking for a reliable supplier online, you might have found both Alibaba and AliExpress as two ways to source products. These two solutions are connected as trading companies. The one that you need will depend on what you’re looking for.
Alibaba asks you to deal with the manufacturers selling quality products in large quantities. However, if you shop with AliExpress, you’re dealing with branded products that you can buy in single quantities and get shipped through companies like DHL and USPS depending on the company.
AliExpress is essentially the standard retail version of Alibaba. Where Alibaba has a MOQ and other requirements, AliExpress allows you to buy like any other customer (read our full AliExpress review). You can use your credit card to buy just one item at a time, from locations like Guangzhou, and get them shipped straight to the United States.
How Does Alibaba Work?
Alibaba is a wholesale company, so you can’t use it to sell things like intellectual property for your eCommerce business.
The model that Alibaba uses is different from other major players like Amazon and eBay. Instead, this company focuses on the trade between companies. Using a business-to-business approach, Alibaba focuses on giving companies access to the large-scale purchases they need to sell dozens of products at once around the world.
The important thing to remember about Alibaba, is that there are different qualities of products available. Despite Alibaba’s trade assurance practices, you still need to do your due diligence. You’ll have to spend some time looking for any red flag that may indicate a seller isn’t as reputable as they should be. This often means conducting a lot of research before you continue with your business strategy.
Registering as a seller on Alibaba is free, and you can deliver up to 50 displayed products. The marketplace that you’ll be involved with won’t handle your sales for you. Once you receive a request from a buyer for an order, it’s up to you to process the payments and iron out the details separately. You can do this through things like Alibaba chat and email.
The good news is that Alibaba doesn’t charge any commissions or transaction fees. Instead, you just pay for the gold supplier membership if you stand out as a certified customer.
If you’re buying products from Alibaba, it’s often a good idea to go for sellers with the gold supplier standard, as this will increase your chances of getting better quality.
Is Alibaba Safe?
It’s difficult to know for certain whether any company is 100% safe when you’re experimenting with things like wholesale and dropshipping sales. However, most people agree that Alibaba is relatively safe, provided that you do your due diligence to protect yourself.
Manufacturers on Alibaba often set things like a high minimum order quantity to protect themselves from issues with buyers. That means that you can’t just buy a smaller quantity to check the items before you jump in. This means that you’re going to need a reasonable budget to get started.
Another thing to consider is that for suppliers located in Shenzhen and beyond, you may not be able to get a phone number, so you can’t always follow up effectively if anything does go wrong. You’ll be restricted to conversations over email and instant messenger.
Unlike wholesales elsewhere in the world, Chinese wholesalers don’t always use as much stock. Suppliers sometimes source products on demand, which means that it takes a lot of time to get everything sorted out so you can begin selling for your business.
It’s also worth making sure that you know whether you can negotiate the terms of your sales with the wholesaler before you start signing up for agreements. Only some businesses will allow you to customize orders.
How to Make Alibaba Safer
If you’re concerned that Alibaba might not be the safest way to launch your business, there are a few things that you may be able to do to protect yourself.
For instance, when you’re hunting for products to purchase on Alibaba, it’s a good practice to filter your search with things like the gold supplier, assessed supplier, and trade assurance options.
A gold supplier is a company that has made a commitment to providing the best services and products available. Suppliers working with Alibaba will pay a monthly subscription fee to maintain this status for their profile. It’s best for you to look for gold suppliers who have been selling for a long time when you’re making your choice.
Keep in mind that this isn’t always a sign of absolute verification, however, as the status is something that a supplier buys, they don’t just earn it.
You may notice that a supplier on Alibaba has the legal status checked note on their profile. If this is the case, then Alibaba has done some research and found out whether the company exists in real-life. An employee will have verified and visited the physical location of the supplier’s business address.
Although this creates an extra layer of trust, it’s important to tread carefully. After all, it’s possible for someone to rent offices or buildings for a day or two anywhere in the world.
You may also want to think about what it means to access a secure payment system with Alibaba. The Secure Payment solution gives the illusion of security to first-time buyers in the B2B marketplace. IF you’ve heard of the escrow system, then this is a similar process.
Within the contracts that are given with Alibaba, there are many loopholes that suppliers understanding the system might use to their advantage if you experience any problems with them. These suppliers aren’t actually doing anything illegal when this happens.
Because the average Alibaba buyer doesn’t always take a lot of time to figure out how everything works, there’s a possibility that they could run out of money and make a few mistakes.
As well as checking the secure payment solution, you should also look into any references that the company that you want to buy from might have. When you’re just about to spend thousands of dollars in capital with someone that you haven’t met before, it’s important to do as much background checking as possible.
One simple way to build trust with a supplier is to ask for a US-based or UK-based reference. If someone refuses to give you these references, then it might be a sign that you can’t trust the company. You could even start by looking up the company name and email address to see if you can find out more about the brand that way instead.
Trade Assurance Can Save You Money
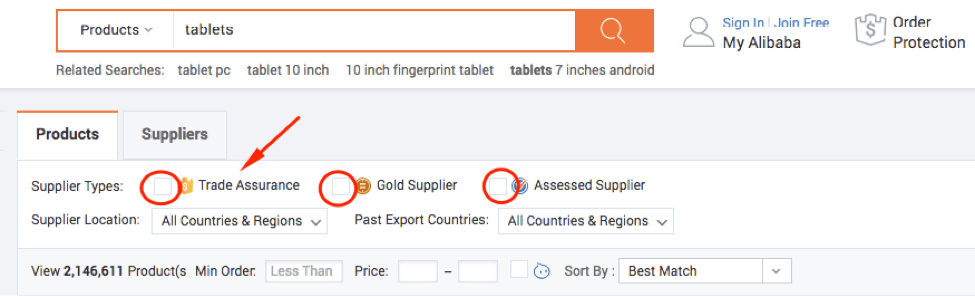
So there you are, ready to search for your next business supplier.
You will now be presented with a filter underneath the search box- make sure you tick all three of them, especially ‘Trade Assurance'. These three boxes are pretty much the first steps to finding good suppliers on Alibaba.
Trade Assurance can be considered escrow protection as the money you send will go directly to the supplier's bank account, but if something goes wrong you’ll have some form of protection.
Choose Gold Suppliers
What’s so special about Gold Suppliers? I'm glad you asked.
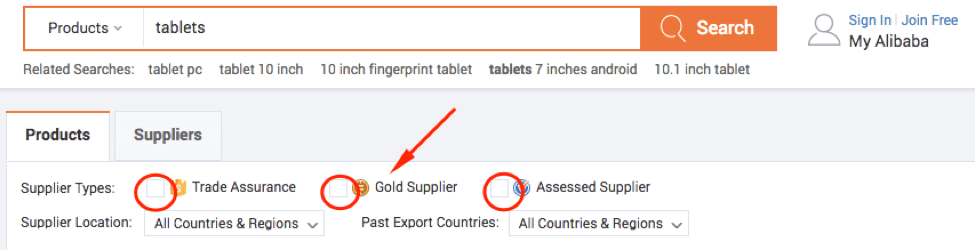
The truth is:
There are still some nasty gold suppliers that can get your order wrong or give you a hard time, but a Gold supplier is a membership that’s exclusive to select sellers on Alibaba. They get more product exposure and other perks from Alibaba.
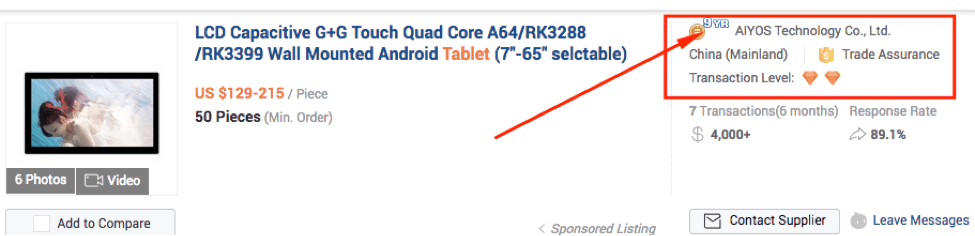
The Gold Supplier membership is expensive, so it should offer a baseline of protection against scammers. After all, they worked hard to get there. A better way of using the Gold Supplier rating is to use it in conjunction with the number of years they have been aGold Supplier for.
The longer the better, like these guys for instance:
Make Sure That There Has Been a Supplier Assessment
Here is the third of those three magical checkboxes and quite possibly the most important one out of the three.
Some say that the onsite check is alright, but if you really want that added layer of trust, it won’t hurt to only select suppliers that have had a Supplier Assessment.
A Supplier Assessment basically means that a third party has checked out the company and its factory. Getting this assessment is difficult, but you can sleep better at night knowing that you’re dealing with a business that has gone over and beyond to be recognized for their export prowess.
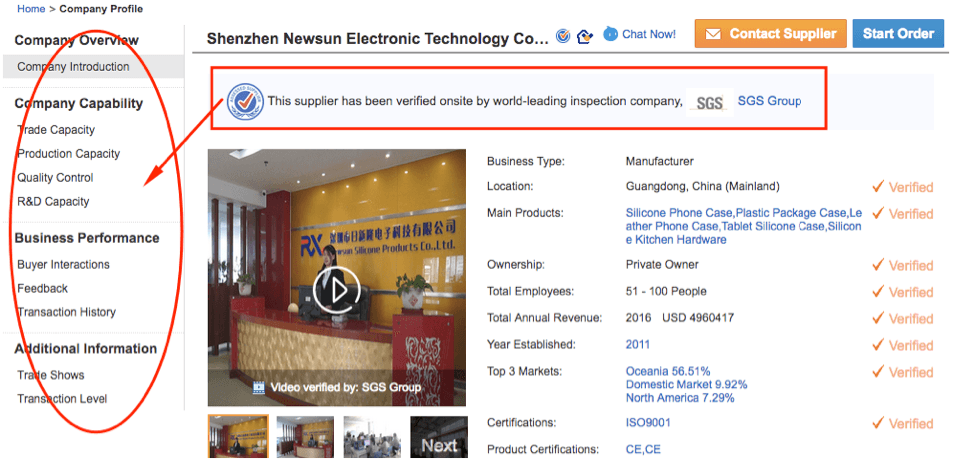
For example, this company when viewed shows that it has been verified onsite by a third party inspection company.
To the left, you’ll find details about their capabilities, business performance and some other additional information such as the trade shows they have been a part of.
Validate What They’re Saying About Themselves
If you have a contact in China that can validate the company, great! If you can go to the factory itself, even better!
However, most of us will find that going to China would defeat our economies of scale altogether, but there are ways to validate a company without leaving your couch.
You’ve ticked off Supplier Assessment and are sure about your third-party validation.
A whois lookup will shed some light on the ownership of their website, check out their email and see if anything is suspicious.
You can also use Google to check out their company name alongside the word “scam” or “fraud” in quotes.
What Are Other People Saying About Your Supplier
Let's stop for a second:
Remember how you asked around about that special someone before you got married/started dating?
It’s the same thing with business and dealing with suppliers on Alibaba. Asking around is generally a good practice especially if you want to start a business relationship.
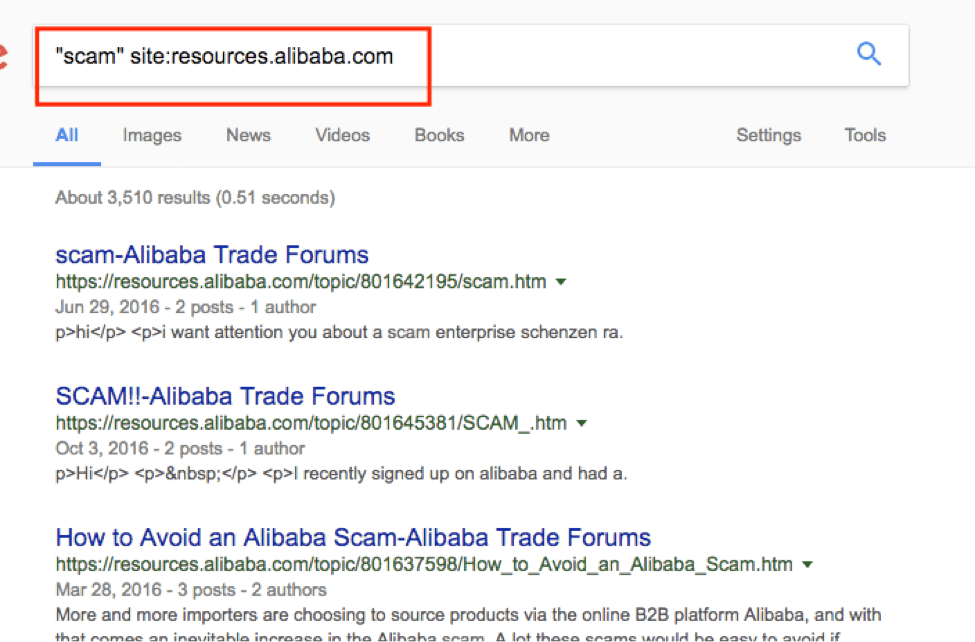
There are plenty of forums, but a good forum to check out a supplier, a category or a product is the Alibaba forum itself.
A simple Google search such as the one shown in the below screenshot isolates all your queries using quotation marks to the respective Alibaba forum.
Don't you just love these search engine operators?
You Cannot, I Repeat, Cannot Buy Branded Items Wholesale From Alibaba
Here’s the deal:
If you’re buying branded items from Alibaba, keep a strict eye on your supplier.
Parent companies of branded items have strict distribution policies with their factories in China.
So if someone claims that they can export branded items in bulk, it's probably a scam.
Check Out The Company’s History
Use this at your own discretion. Next to the information on the specific product that you’re looking at you’ll find this:
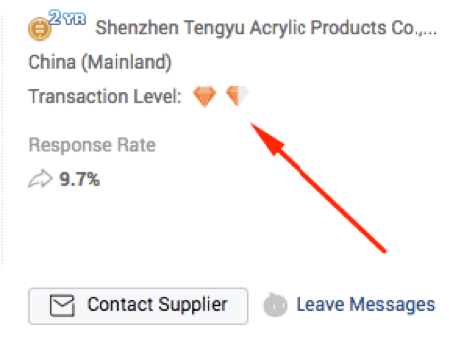
These diamonds are an indication of transaction-level points obtained by the company for their transactions awarded by Alibaba.
Alibaba explains these:
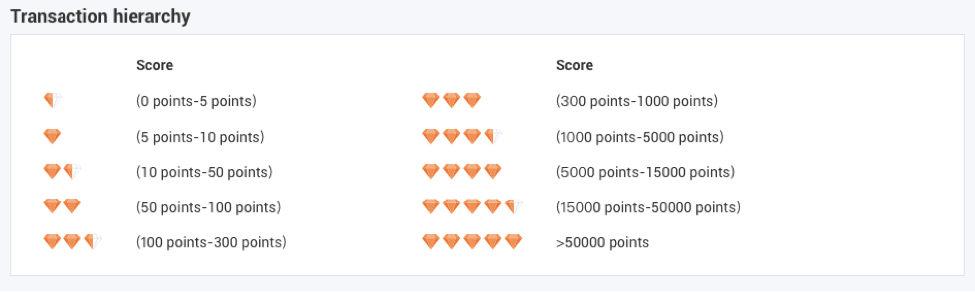
According to Alibaba, the Trading Level is, “based on an accumulated score awarded for total online transaction volume and amount”.
The higher the score, the better the volume and amount so to speak.
Also, when you go to the company page there is usually a section called Transaction History. Here you’ll find a summary of how many transactions they’ve processed in the year.
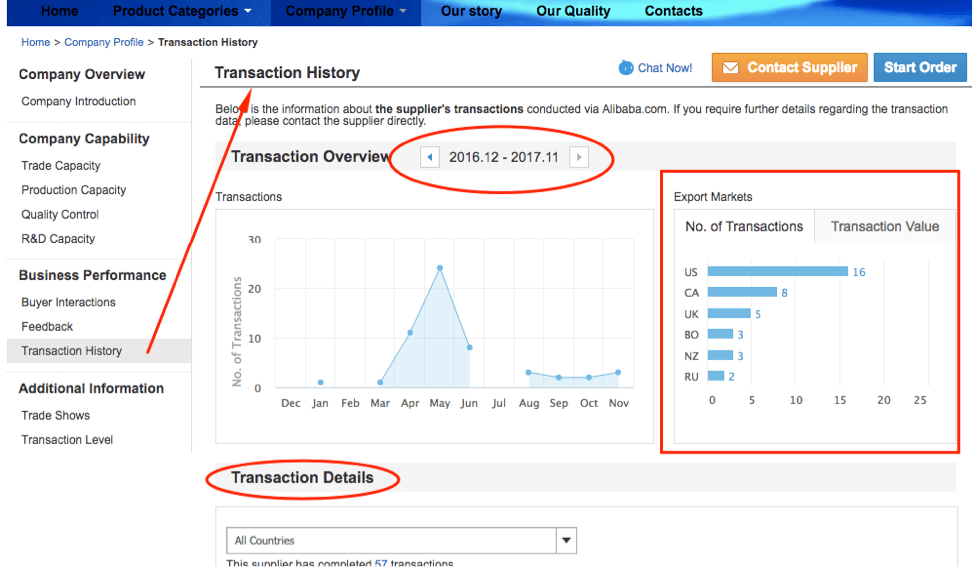
There are two ways to interpret this data, one is that you can probably trust a company that has made a lot of transactions in the past.
I mean, why don't you?
Bigger transactions pretty much mean that they’re currently in the business and that they’ve been in the business for a while now.
You could also be looking for a new and reliable company which doesn't involve in scamming practices and really sells quality stuff.
The decision is entirely up to you, but usually, I'd almost always pick those with substantial transaction history.
There’s a Difference Between Manufacturers and Traders
I understand. So many choices.
A manufacturer will be able to offer you a better deal since what a trader does is, well, just trading. If you’re looking for a long-term supplier you’re better off looking for a manufacturer rather than a trader of goods.
They’ll be able to offer you more competitive prices and you’ll be able to develop a relationship with them in the long run- which comes with a lot of benefits!
Order a Sample Before You Go All Out
Don’t be part of the statistic. We know a lot of people who’ll find a great deal from a legitimate supplier and just start ordering 100,000 units without even having a first evaluation. It doesn’t work like that.
Ever bought a suit or a dress without trying it on? Nope. Everyone has an “it looked different online” story and you don’t want one, especially in any large-scale business deal.
It’s the same thing, you’ll want to be a good business owner and part of that process is verifying that your product lives up to your standards. Failure to do so is a recipe for an early loss of revenue.
It’s All About The Money
This is a part that you don’t want to mess up, so pay attention. A bonafide company will have multiple options for you to pay, and as we said earlier it’s sometimes more desirable to transact with companies that offer escrow via Trade Assurance.
Make sure you’re very clear about everything that’s been stipulated in your negotiation including any hidden costs or anything in fine print.
You’ll receive an invoice once you’re done negotiating the odds and ends of your supply and make sure that all the details match as what's mentioned in Alibaba.
If PayPal is an option, then pay via Paypal.
Make Sure You’re Ready To Receive The Shipment
Take a moment to think about how the goods will reach their destination.
You’ll have practice with the sample product you’ve asked them to ship you if that’s the case. Some vendors will be able to arrange all the shipping for you, but you have to make sure that they do.
You can hire a shipping broker to help you out should you have any specific concerns about importing and what not.
However, a quick way to find out more information is to ask the vendor itself. The price of shipping may surprise you, but sometimes you’ll find that they have bundled it along with the cost of your goods.
Alibaba Review: Conclusion
So, there you have it, if you follow these simple rules, you’re on a good track to find your ideal supplier, whilst being on the safe side. Remember, trust your instincts, and your gut is usually correct.
Alibaba can help you set up your own dropshipping business when done right. If that's your case, visit our article “The best way to Setup a Drop shipping Business Quickly” to learn more before getting started.
In any case, always ensure that the supplier has a return policy, before placing the order. Things can go wrong and if the shipment never arrives, you'll have to raise a dispute with the shipping agent.
Buying from Alibaba is an easy task but safe only if you do it with precision.
What have you bought from Alibaba in the past? How long did it take? How was the process? Share your Alibaba stories in the comments below.




I have been getting a company on Alibaba to make my buckles for my leather bags that I make. (I chose them carefully) Trust is definately an issue. I sent my buckle to the manufacturer, they still didn’t get it right. they promised to get the next order right😳. thinking ok give them another shot. Quality Control was out the door. The pre-ship photo looked good. When I received them they had missed the final touch of a protective coat, which doesn’t show up on a photo. Anything can go wrong with these guys. Never again. No responsibility terrible QC
Sorry to hear about that Regan.
Hi , Bogdan … going by your name you should be Roumanien . I came across this, looking for reviews on Alibaba . Are you acctualy working with them or just giving people advise about them ….
Hello Lavinia,
No, we do not work with them, we are an independent review website.
Hello. I would like to order from Alibaba but products that are put up for sale by manufacturers in Europe. What are the costs and can I buy a larger quantity per individual?
Hello Florin, you will need to check with the manufacturer.
Hello. Very useful article. Thanks alot.
Regards
Maria Ahmed Hussain
You’re welcome Maria!
Good article, full and detailed explanation. I want to buy electronic equipment, such as smartwatches, AirPods, wireless horns, charging discs, among other things for my small business, doing accounts, the truth is that you can see a huge profit since really, the prices of the products In Alibaba they are very cheap, but the reality is that I have heard scammed people, and to the acquaintances that I have, I have asked them if they have ordered through Alibaba but no one has bought there, they all tell me that they are asking for Amazon.
I have been looking for tutorials, and there is a way to make sure that the supplier is reliable, and that is that each store must have a digital stamp in which it says that Alibaba was in that store, it is as a way to make sure that it really exists and They are trustworthy people, another advice I got is to buy from a store that has been publishing on Alibaba for more than 3 years, that way we make sure that if it is still there, it is because it has not presented problems.
The information posted here has helped me a lot, thank you.
Thanks a lot. Great article.
You’re welcome Trevor!
Hi there, just read your review, very informative thank you but I’d like some more info on how shipping works with Alibaba. I only see their shipping costs on some items and it can be so expensive, even for a sample piece. Is this correct or is there a cheaper way to ship? I’ve seen reviews where you can ship yourself but I don’t see an option for this. Any help appreciated. Thank you.
Hi Bogdan, thanks for the article, I’d like to start selling my producst in Alibaba as a trader, how possible is that considering that I’ll start with 0 reviews?
Hello Ariel, I really don’t know what to say. But you should give it a try and see how it works.
This was a great read. I’m thinking of purchasing 1 electric bike to save some money. I Will use all your suggestions as I navigate the Alibaba website thanks again for taking the time out to write a very informative article on the safest ways to navigate through Ali Baba
Good luck with your purchase Chris!
Cómo puedo hacer los pagos en alibaba tengo una transacción completa hecha de compra pero no he podido hacer el pago porque no entiendo cómo hacerlo
Bogdan Rancea thank you very much, so helpful and I feel more comfortable in taking the next steps.
You’re welcome Francis!
Thank you for the article
Much helpful
You’re welcome!
I’m new to buying on Alibaba and I’m terrified. This article helped a lot. I’m still a little scared the shipping prices are crazy.
This is awesome! This article is not only helpful but also so much educating! I love the fact the author explained each and every aspect you have to know before dealing with the sellers on alibaba and some principles apply on other shopping platforms too. Kudos! I want to read more of your articles. They seem so very helpful!
You’re welcome Rhion!
I want start my own brand of lashes but I want to start with 100 pairs . I need buy more for found a good offert?
Samples are hard to get I already tried 3 different companies
I just downloaded Alibaba and I saw all the unbelievable prices and I became concerned. On enquiry from Google, I lead led to this article. The article is more than helpful. Thank you.
You’re welcome Moses!
Éste artículo es importante para mí primer compra
Gracias.
You’re welcome Evangelina!
Exactly the article I was looking for.Thank you for the sarticle
You’re welcome Ernest!
Hi, any idea how much UK will charge for tax and customs when items arrive here in UK?
I’m buying weight lifting goods total 728kg in dumbells. Cost $1100
Regards
Kam
Hello, it depends on the country you are importing from.
Very informative. Thank you very much.
You’re welcome 🙂
Im planning to buy laptop on alibaba.com for personal use, why is it so cheap? Isn’t original or authentic?
Thanks for sharing those steps. I’ll start exploring now.
Good luck Bob!
This was really helpful, thank you very much
You’re welcome!